Offensive Security
Offensive Security
- Penetration testing
- Black / Grey / White box
- External, internal and remote access testing
- Purple team
Proactively protect your computer systems, networks and individuals from attacks.
Penetration Test
The goal of a penetration test is to evaluate how well a company, infrastructure, data and employees are protected against real-life attacks. The penetration test with Hacknowledge is not a classical vulnerability assessment. It is conducted the same way as a targeted attack, by trying to breach the defense systems in place and to exploit the vulnerabilities found during the test. Hacknowledge Offensive Security team elaborates a cartography of the paths that a real attacker could take in order to attain their objectives and cause harm to the targeted company.
In other words, the penetration test focuses more on the way an attacker is able to break a company’s defenses than specific vulnerabilities.
By using the same tactics as an attacker, Hacknowledge will help you answer these questions:
- Which of my systems are vulnerable?
- Which information can an attacker retrieve on these vulnerable systems?
- To which extent can an attacker penetrate inside my network and what could be the impact?

With Azure Lighthouse, we can deliver managed services using comprehensive and robust management tooling built into the Azure platform to manage your Sentinel alerts into our SOC service.
Our Approach
Offensive security services are part of our full VISION service or can be purchased separately
Our Approach
Hacknowledge proposes three different approaches in order to conduct the penetration test. Hacknowledge uses well-known methodologies such as OWASP, OSSTMM, PTES and PSSA for their assessments. These references are used to identify, classify and report vulnerabilities according to current industry standards.
Using any of those approaches or several combined, Hacknowledge proposes a panel of different tests to cover your whole infrastructure:
- Web applications & APIs testing
- External, internal and remote access testing
- Wireless penetration tests
- Physical security assessment
- Phishing tests
A report will be presented and provided at the end of each mission and will include: an executive summary, full technical details of findings, description of attack scenarios, source code of written proof of concepts and simple steps for remediation.

Black Box
The penetration testers do not have logical access to the targeted assets. They do not have any knowledge about the systems to attack before the engagement and do not possess any user accounts, if applicable. The goal of this approach is to simulate an opportunistic attack against your company’s systems.
Grey Box
In this approach, the penetration testers have a general overview of the systems to attack. They are usually given a type of initial access such as accounts, and may possess further knowledge about the global infrastructure and network behind these systems. Greybox tests simulate the level of knowledge that an attacker with long-term access would achieve, or any party with low access privilege would have.
White Box
The penetration testers have all information needed to acquire a deep understanding of the systems they target. The nature of this test allows a close relationship between the testers and system owners. This approach is mutually beneficial as it helps the testers to focus on the more important issues and at the same time aid in fixing those issues. This type of test unveils hidden vulnerabilities that can be used in more sophisticated targeted attacks.
With Azure Lighthouse, we can deliver managed services using comprehensive and robust management tooling built into the Azure platform to manage your Sentinel alerts into our SOC service.
Advanced Exercises
Hacknowledge can also conduct more advanced testing
Advanced Exercices
Hacknowledge can conduct more advanced testing that will provide a more in-depth view of border protection, employee awareness and how well processes and procedures cope when faced with a real attack scenario:
Adversary Simulation
Adversary simulation is a specific type of red teaming engagement where our engineers will mimic the Tools, Tactics and Procedures (TTPs) of adversaries your organization is facing.
It simulates a targeted cyber-attack that mirrors the way a hacker works. It reveals how effective your organization’s defenses are against an attack and pinpoints the bad practices that leave you open to a cyber-threat.
Adversary simulation evaluates the effectiveness of its security defenses, including people and processes, using different scopes and permitting to identify a possible “kill chain”.
Red Teaming
Our Red Team will test your entire security defense. It assesses an organization’s capability to detect and respond to these threats. A Red Team with Hacknowledge consists of 4 phases.
During the preparation phase, the engagement for the Red Team exercise is formally launched, and the Red Team leader (assigned beforehand) starts liaising with the participating entity to establish the scope and the flags for the exercise.
Once the scope has been agreed, the testing phase should commence with targeted threat intelligence in order to evaluate the attack surface across the entity and the relevant threat actors and probable threat scenarios. At the end of this phase, attack scenarios should be fully established.
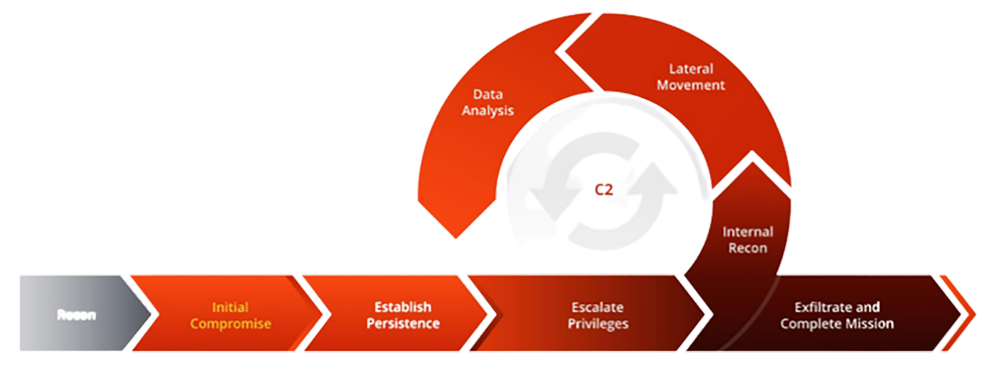
Following completion of the targeted threat intelligence process, Hacknowledge Offensive Security Team will try to compromise the targeted systems and services that underpin each critical function included in the scope.
This process can be resumed with this graphic. At the end of the lifecycle, the Red Team should have captured the flags agreed during the scoping phase (and possibly updated during the threat intelligence process).
Purple Teaming
Same as Red Team with additional collaboration with your Blue Team (defender’s security team) for a better understanding of possible attacks on your infrastructure and increase your detection capabilities. This exercise is ideal for companies that already monitor their security.
Hacknowledge follows the TIBER-EU framework guidance for their Red Team and Purple Team engagements, specifically created for supranational authorities and financial companies.
Phishing Tests
We agree on a customized email to send to your users to test and raise their security awareness using credential theft or payload delivery.


